Description
Elevate Your Web Security with Cutting-Edge AI and Machine Learning
In an era where digital threats evolve at breakneck speed, traditional security measures no longer suffice. Enter BitFire, the revolutionary WordPress firewall that harnesses the unparalleled power of Generative AI and Machine Learning. This innovative solution marks a significant leap forward, offering a bespoke security strategy tailored to each individual website.
BitFire introduces a pioneering “block by default” model, setting a new standard in proactive defense. By generating a unique allow list for each site, it ensures that only legitimate traffic gains entry. This approach blocks zero-day attacks instantly, without the need for frequent signature updates. It’s not just a firewall; it’s your website’s personalized guardian, designed to distinguish between friend and foe with unprecedented accuracy.
While traditional firewalls operate on a reactive basis, allowing all traffic except for known threats, BitFire flips the script. The old way exposes your site to the latest threats until updates catch up, a delay that can be critical. BitFire’s AI-driven model adapts in real-time, offering immediate protection against even the most cunning of digital adversaries. This means you can update and patch at your leisure, without the panic-driven updates that come with new vulnerabilities.
BitFire isn’t just a product; it’s the culmination of over two decades of frontline web security experience. Our legacy is built on the expertise of a visionary computer security architect, whose strategies have defended the digital realms of leading corporations and critical infrastructure alike. With BitFire, we’re extending this unparalleled defense to your WordPress site, providing peace of mind in an unpredictable digital landscape.
Welcome to the future of web security, where BitFire leads the charge against emerging threats with intelligence and precision. Secure your site with BitFire, and enjoy the confidence that comes from knowing you’re protected by the best.
🚫 0-Day Protection for all critical vulnerabilities
You need a security product that can protect you from vulnerabilities before they are disclosed and before you can upgrade. BitFire is the only WordPress security plugin that has protected from every critical 0-day vulnerability since 2022.
🌐 Unleashing the Power of Fingerprint Intelligence
Imagine a security net that instinctively knows friend from foe. BitFire boasts a repository of over 3,000 known, authenticated, and helpful bots, each carrying a passport to your trusted realm. Only humans and your sanctioned partners hold the keys to your digital domain.
💎 Battle-Tested Brilliance
BitFire RASP isn’t just theory—it’s proven. Battle-tested against every critical 0-day WordPress security vulnerability of 2022-2023 (CVSS Score 8.0+), our firewall consistently thwarts even the craftiest exploits. Sleep soundly knowing that your WordPress fortress is fortified with an unyielding shield.
🤝 Partnering with Giants, Analyzing Trillions:
BitFire stands on the shoulders of innovation giants. Collaborating with web analytics pioneers, we’ve delved into the digital landscape, meticulously dissecting over 100GB of unique request signatures. The result? Over 1 trillion one-of-a-kind fingerprints etched into our advanced bot detection technology.
🚀 Performance with Purpose
Unlike clunky traditional WAFs that trudge through huge rulebooks, BitFire focuses on what matters—every request’s intent. We don’t slow down your site with unnecessary inspections; we optimize your speed without compromising security. In fact, we run 20X faster than WordFence!
🌐 Deep Integration, Blazing Speed
What sets us apart? Our RASP firewall’s deep integration with WordPress and PHP. Every SQL query, every file access is meticulously inspected to ensure your code and database users remain untouchable. Our deep integration with WordPress core and PHP internals ensure we’re not only secure; we’re blazingly fast.
🔒 Security Meets Simplicity
We believe in power without complexity. BitFire RASP empowers you with advanced security that’s as easy to deploy as it is potent. Your site’s defense is now a seamless part of its structure.
Ready to revolutionize your website security? Join the BitFire movement and let’s ignite a new era of web protection. Elevate your WordPress security—because when you have BitFire, you have fire on your side.
HACKER / SPAM / BOT / BLOCKING [FREE]
- Deep insight into your website’s security.
- Monitor traffic and perform security investigations at lightning speed.
- Deep file analysis malware scanning can find unique malware with ease.
- Human / Bot identification identifies 99.5% of all web attacks.
- BitFire verifies every web request to your site is from a real human or an approved bot. Hackers / Spammers and Scanners are blocked the first time, every time.
- BitFire’s request fingerprint technology can easily identify the difference between a real browser and a bot without requiring any captchas or user interaction.
- BitFire maintains fingerprints for thousands of web browsers, and over 3,000 known good bots.
- Real-Time IP reputation data for over 300,000 known abusive IP addresses supplements bot classification for unknown bots.
- There are over 4 trillion unique BitFire request fingerprints and only one matching each unique browser.
- Identify and block ANY hacking tool, by signature not just user-agent.
- Block plugin/theme enumeration from tools like wpscan, nmap, nikto, etc.
LOGIN SECURITY
- BitFire uses browser fingerprinting to detect Phishing attacks against your login page and blocks them.
- No new apps to install on your mobile device.
- No account lockouts and waiting for lockout expiration.
- BitFire blocks brute force attacks by identifying the difference between a real browser and a bot and blocks all bots accessing login systems.
- BitFire emails login links for any account with 2FA enabled to prevent login abuse.
LIVE TRAFFIC MONITOR [FREE]
- Observe traffic with city level geo-location, IP, User-Agent, Request Rate, Referrer, Response Code and Query Parameters.
- Filter traffic by IP, user-agent, url, or response code.
- Bot detection for over 3,000 known bots and over 180 known web browsers.
- Lookup detailed IP abuse data for any request.
- Observe each request and the BitFire response
- Add only 2ms after each request to log to our binary log file
- Log up to 512 requests [FREE], or 32,000 requests [PRO]
SECURITY HEADERS
- Rated A+ by securityheaders.com
- BitFire includes all up-to-date headers to secure the browser.
- Content Security Policy ️(CSP)
- Permissions Policy ️
- Prevent Client-Side redirect attacks
- Auto configured CSP, BitFire learns every included domain and configured CSP for you [PRO]
Configurable Malware Scanner [FREE]
- BitFire has one of the highest malware detection rates in the industry.
- Database of 10,000,000+ valid wordpress plugin and theme file hashes.
- Scan up-to 10,000 files per minute with our unique fast-hashing technology.
- Professional US based security experts to perform hand malware removal if needed ($128.00 USD).
Web Application Firewall
- BitFire has a highly rated Premium WAF which includes a real PHP, SQL, HTML and JavaScript parsers not just a huge list of regular expressions. This allows BitFire to detect and block attacks that other WAFs miss, without false-positives. Testing by: https://labs.cloudbric.com/wafer
- BitFire [PRO] – 🇦 (94%)
- MalCare [PRO] – 🇫 (34%)
- WordFence [PRO] – 🇩 (41%)
- iThemes Security – 🇫 (2%)
- Ninja Firewall [PRO] – 🇩 (67%)
- Site Ground Security – 🇫 (2%)
- Shield Security [PRO] – 🇫 (2%)
Runtime Application Self Protection
- Runtime Application Self-Protection (RASP) monitor’s your plugin’s actions and prevents them writing unauthorized files, or created un-authorized users.
- Only RASP created for WordPress that monitors all vulnerability vectors.
- Integrates with WordPress and PHP inspecting all SQL queries and file access.
- Prevent vulnerabilities from exploiting and installing malware or backdoor accounts.
- FileSystem RASP integrates with PHP interpreter to prevent any PHP file writes.
- Database RASP inspects every query that modifies the Database and prevents any vulnerable plugin from installing backdoor accounts.
- Network RASP monitors server network requests, identifies and blocks SSRF and also MITM credential theft attacks (Evil Nginx, etc).
- Authentication RASP monitors authentication and prevents any vulnerability from escalating user privileges.
Privacy / Monitoring / Data Collection
-
Privacy. We take privacy very seriously. BitFire inspects all traffic going to the webserver and takes care to filter out any potentially sensitive information by replacing it with redacted. The config.ini file includes a list of common sensitive field names under the “filtered_logging” section. You can add additional fields to filter in the config file by adding a line “filtered_logging[field_name] = true” and replacing “field_name” with the name of the desired parameter to filter.
-
BitFire includes an error handler which monitors it’s operation. In the event an error is detected only in the BitFire software; including during install, an alert can be sent to BitFire’s developer team. The development team monitors these errors in real time and includes fixes for any detected errors in each new release.
-
Malware scanner. BitFire sends tiny 64bit hashes (signatures, or fingerprints) of every file to our hash database. For instance, index.php may hash to the number: 812612388126487. The database is many gigabytes and centrally located on our servers. BitFire uses that information to determine if a file has been modified or is a known good file and sends the results back to your site. Client hashes are never stored off your server.
Screenshots

BitFire shows the source location, time and response for every web request to your site. See good and bad actors in real-time. 
Bot Control page allows instant authentication of over 3,000 known bots and 300,000 malicious IPs. 
Detailed malware scanner contains over 20 million data-points and scans 10,000 PHP files per minute. 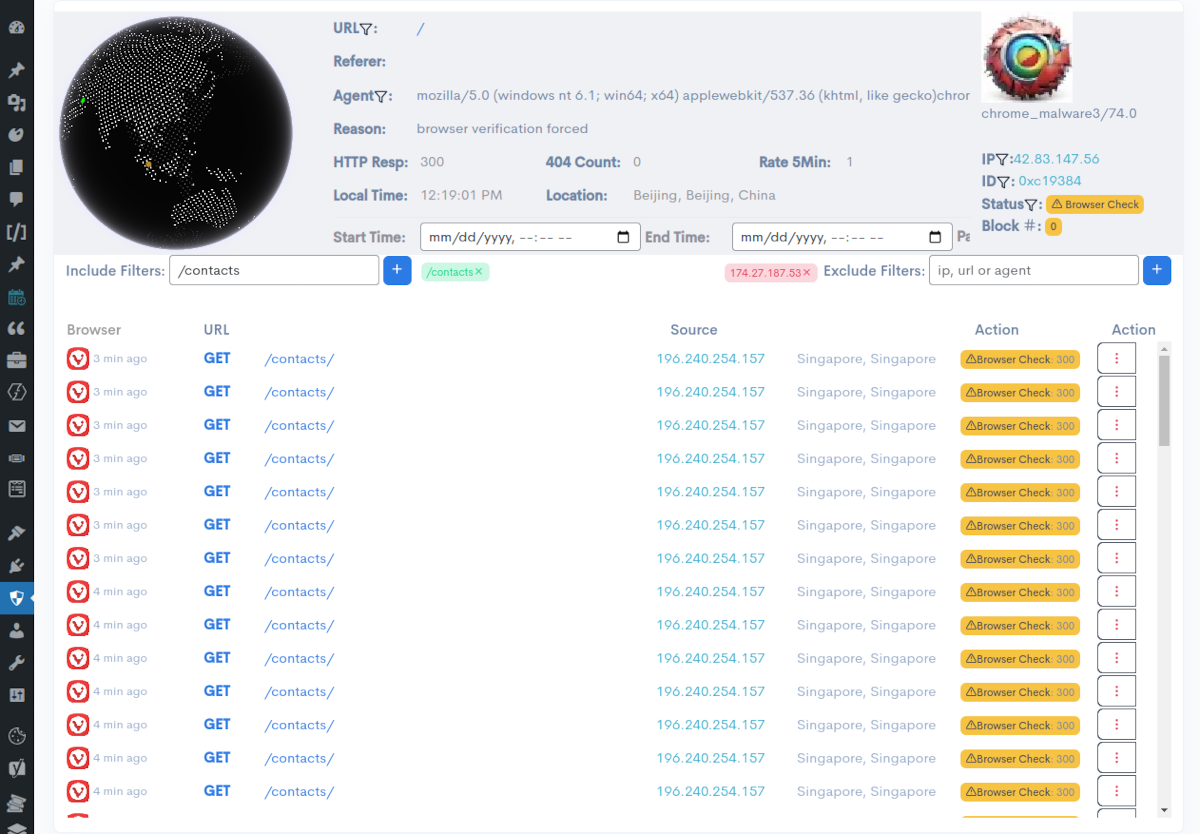
Search for any web traffic by time, user-agent, url, IP or response. Identify correct web blocking and website functionality. 
Database malware scanner with backup and restore points can identify malware comments and posts from over 2.5 million domains. 
Plugin monitoring alerts you within the hour when new plugin vulnerabilities effecting your site are released so you can stay on top of important security updates. 
Simple on/off configuration with granular rules can be set to alert to test new rules before actually blocking.
Installation
After installing, you can configure the plugin by clicking the “BitFire” -> “Settings” menu item in the WordPress admin dashboard. You may choose to run the plugin in “Always On Mode” (WordFence: “Optimized” mode) by clicking the “Always On” button on the settings page. This will add bitfire to your PHP’s auto_prentend_file list and ensure that BitFire is always running on your site.
Note, not compatible with Windows Operating systems.
FAQ
-
What is the difference between FREE and PRO versions?
-
BitFire free includes our real-time event log, A+ rated security headers, malware scanner, and complete bot blocking which blocks 99% of all Internet threats.
PRO includes our Runtime Application Self Protection (RASP) firewall to prevent vulnerable plugins and themes from executing on your site along with our A+ rated WAF. -
Can BitFire RASP protect my website against zero-day vulnerabilities?
-
BitFire has a 100% track record for protecting against every critical 0-day WordPress security vulnerability since 2022 with 0 new signatures required.
-
Why do other plugins focus so much for Malware Scanning and Cleaning?
-
Great question. Notice how much extra other plugins charge you to clean up malware and how much of their product is focused on finding malware on your system?
They don’t do a great job of keeping malware off your site, and then charge you extra when their security fails. -
How much is PRO Version?
-
WAF only version is $79.99 / year, and complete RASP protection is $128.00 / year.
-
If other security plugins live up to their hype, why do they scan my site for malware daily?
-
That’s an excellent question. The majority of popular security plugins create custom signatures for each WordPress plugin vulnerability as they are publicly disclosed. With over 10,000 known WordPress security vulnerabilities and less than 200 signatures, they miss blocking a lot of hacks. They are also unable to block the most common security flaws (access control errors) for anything they do not have a pre-built signature for. To make the situation more difficult, they delay these rules by up to a month for non-paying customers.
-
How does Redirection Protection work?
-
Our unique software keeps track of every 3rd party domain your web page uses (Facebook, Google, JavaScript APIS, themes, etc.). After several weeks of learning, CSP security headers are sent to visitors instructing their browsers to only use or redirect to your approved domain list.
-
Does BitFire prevent Cross-Site Scripting (XSS)?
-
BitFire includes outstanding XSS protection, including HTTP headers and content filtering for persistent, reflected, and DOM-based XSS attacks.
-
Does BitFire block SQL Injection attacks (SQLi)?
-
Yes. BitFire has advanced SQL parsing similar to MySQL syntax parsing and can understand SQL queries regardless of encoding, injected comments, and other evasion techniques.
-
What are some examples of RASP blocks?
-
- Adding a new administrator account? BitFire checks that the current user has the administrator privilege before allowing the account creation.
- Making a network connection? BitFire checks the remote system against a list of over 2.5 million malware domains before allowing the connection.
- Adding or editing a file? BitFire inspects the filename and content to ensure that it does not edit a PHP file or inject backdoor code.
- Redirecting the visitor to another website? First check the malware domain list before sending the redirect.
- Is a plugin eval() dynamic PHP Code? Inspect the code being passed to eval() and block malicious code before executing it.
-
Why shouldn’t I use WordFence?
-
If you use WordFence, you should only use the paid version. WordFence has a team monitoring emerging WordPress vulnerabilities and writing custom rules to block specific exploits. They are very good at it and run a great blog on their work. Paying customers receive these virtual patches as soon as they are available. Free customers receive the patches 30 days later. If your website is vulnerable, it is almost guaranteed to be hacked before the patch is available to free customers. Don’t leave your site at risk.
-
Is BitFire RASP easy to install?
-
Yes, BitFire RASP offers a seamless integration process tailored for WordPress. The setup is user-friendly, and our support team is always ready to assist.
-
How is BitFire RASP different from other security plugins?
-
BitFire RASP is the only RASP firewall available for WordPress. It’s crafted to provide real-time protection by deeply inspecting your site’s activity, ensuring comprehensive security without compromising performance.
-
Can BitFire block bots and automated attacks?
-
BitFire’s primary feature is bot blocking which is 100% functional in the free version. 99% of WordPress attacks are from automated tools scanning every domain and IP address for known vulnerabilities. BitFire verifies human web browsers with a JavaScript challenge similar to Cloudflare but over 50 times faster (1/10 second VS 6 seconds). BitFire also includes a list of over 80 search engines and SEO tools that are network verified to ensure only valid bot traffic reaches your site.
-
How do I get support if I encounter issues with BitFire RASP?
-
You can use the WordPress support form or visit our website to access our official documentation, which includes in-depth descriptions of security features, common solutions, and comprehensive help. Our dedicated support team is also available to assist you. You can reach out through our support channels, and we’ll promptly address any questions or concerns you have.
-
Why is BitFire better than WordFence?
Reviews
Contributors & Developers
“BitFire Security – Firewall, WAF, Bot/Spam Blocker, Login Security” adalah perisian sumber terbuka. Orang-orang berikut telah menyumbang kepada pemalam ini.
PenyumbangTranslate “BitFire Security – Firewall, WAF, Bot/Spam Blocker, Login Security” into your language.
Berminat dalam pembangunan?
Layari kod, periksa repositori SVN, atau langgani log pembangunan dengan RSS.
Changelog
4.4.11
- Small bug fixes for some lower end hosting services
- Fix for error on hosts missing mb_string extension
- Added additional browser identification
- Improved support for default csp policy
4.4.10
- bugfix for upgrading cache cache
4.4.9
- Major improvments in quality and performance
- Daily report emails
- Complete rewrite of caching and statistics
- Offline log analysis mode only
- Existing clients receive 80% discount early adopters code via email
- Bug fixes
- Improved browser and bot detection
- FULL SUPPORT FOR CACHED WEBSITES – vastly improved support for websites with front end caching like cloudflair, etc
- Log analysis search improvements
- Log up to 30 days of data up to 2million requests / month!
4.1.15
- Resolved issue with saving bot control data
4.1.14
- Resolved issue with malware scanner
4.1.13
- Improved trash bot detection
- Improved and de-cluttered bot control interface
4.1.12
- Improved support for older iphones, ipads and macs
- Removed dead code
- Added feature toggle code for server uptime metrics
- Added server metric logging (blocks, etc)
- Fixed cloudflair compatibility with change in how cloudflair forwards SSL status (infinite redirect loop)
- Improved support for downloading large IP database on limited hosting accounts
- Don’t report unknown empty index.php files in malware report
- Added new browser support ios text messaging, ztunnel, nettype, browserng
- Save fewer junk bots in bot control page
4.1.11
- Improved verification of ajax requests from cached pages.
- Added support for editing CSP policy from settings page!
- Verbiage changes
- Fix a PHP warning for double submitted headers
- Additional fingerprints
- BitFire encrypted cookies accessable from JS to support page caching JS verification
- Add support for client side ray verification under feature toggle
- Renamed cache directory to fix wp-optimize deleting rogue /cache/ directories…
- Several small fixes for rare corner cases
- Fix infinite redirect when SSL un unwrapped and HTTP headers are set incorrectly by upstream proxy or web server
- Fix rare case for detecting PHPSPloit with null or empty header values
4.1.9
- Fix for ajax authentication of cached pages
4.1.8
- Improved malware scanner server communication
- Improved support for auto-healing syntax errors in the config.ini file
- Improved WAF inspection for some special cases for admin which reduces false-positives
- Removed always-on from startup wizard, added security headers to wizard
- Improved labeling of request types on the traffic view
- Added new mode to never check Ajax Requests for bots. This mode is useful for sites with page caching enabled.
- Reordered the settings page, and added new settings for some old features
- Nicer error page for Windows users (Windows is not supported)
- Removed dead code
- Added additional file locked to remove some race conditions on busy servers
- Auto-Healing config.ini files with syntax errors
- Content Security headers are now in FREE!
- Block plugin enumeration is now in FREE!
- Fix link to purchase page
- Fix adding some malware files to the allow list
4.1.7
- Add Content Security Policy and Feature Policy to the free version of BitFire
- Additional file locking to remove possible write conflict
- Fixes for websites with page caching. New mode to skip browser checking on ajax requests.
if the initial page is served from cache, the browser will not be verified on initial ajax requests.
This mode will allow those ajax requests to skip browser verification. - Improved browser fingerprints
4.1.5
- Fix for WP_CLI lockfile permissions web/user
- Added 2 new bot control options to settings
- Fixed a case where some requsts were flagged as “View Only:428”
they now correctly show as “Browser Check:428” - Added check for wordpress /jetpack to not be blocked from the home network
- Added new forced block to prevent bots from login to the human login page
4.1.4
- Fix for removing some manual exceptions
- Added hard exceptions for google, bing and wordpress
- Added additional results for cases where bot and/or browser checking is off
- Added malware exclusions for old updraft backups
- Fix for image dashboard icons
- Fix for settings page scrapper blocking
- Added new setting to change http response code for verification page
4.1.3
- Bugfix for some rare cases that skipped last few files during malware scanning
- Fix for case where BitFire could not identify some WordPress content URLS for icons
- Reclassify unknown files in /wp-content as plugins not core files
4.1.2
- Bugfix for broken config.ini files
- Added blocking xmlrpc calls
- Fix some malware false positives
4.1.0
- Added new fingerprints for Facebook web browsers
- Added new styles of browser verification pages
- Added option to not require browser verification for page views to reduce friction
- Added configurable title tag on browser verification page
- Re-enabled malware scanner!
4.0.10
- fixed issue with adding exceptions on the new dashboard
- added space-bar short cut to update dashboard data
- fixed small double activate bug that would create new cookie names on double activation
4.0.9
- move ip location database to alternate location to prevent re-download on upgrade
- improve proxy cache support for browser verification
- UI fixes
- improved bing detection, added some additional browser icons
- added code to detect cached browser verification page and redirect out
- changed default browser verification http code to 428 to prevent some proxys from caching it
- added code to prevent infinite looping when browser verification page is incorrectly cached
- bug fix for some cases when firewall did not correctly identify logged in administrators
4.0.8
- hotfix for admin check when headers previously sent
4.0.7
- improved upgrade process
- add ip reputation check from abuseipdb.com to dashboard and bot pages
- add support for wp-cli
- added cache prevention headers for browser verification for cloud flair enterprise
- fix for dashboard icon css
- fix for adding user-agent exceptions on the dashboard page
- improved bingbot detection
- purge binary log if corrupted data is detected
- reduce false positive for sql injection
- improved bitfire dashbaord rendering
- added backup learning for browser fingerprints
- added self healing for damaged binary web logs
4.0.6
- bug fixes
- performance improvements
4.0.1
- GREATLY improved browser and bot detection
- Added over 180 browsers and over 300 unique browser icons
- Hard coded Google detection for flawless google verification
- Switched from json log to binary log files to save space and improve performance
- Ability to log all web requests
- Search for any web request by user-agent, ip, url, response code and time
- Added comercial IP reputation DB with over 300K abusive IPS
- Free support for 128 unknown bot IP checks
- Simplified User Interface
- Auto bot blocking for unknown bots with IP reputation DB
- Added device fingerprints for over 3,000 device and browser combinations
- Ability to detect valid browser requests with device fingerprints using no JavaScript
- Reduced the server and browser load for unknown browser verification with JavaScript
- Added IP address and User-Agent white listing
- Improved IP Geo location performance and accuracy to City level
- Removed WordPress dashboard widget until 4.1 transaction
- Removed malware detection while 4.0 database updates… Will return in 4.1
3.9.12
- reduced batch size of malware check based on available memory
- fixed malware false-negative for some uses of ‘passthru’
- Added support for auto decoding base64 encoded data
- improved support for XMLRPC checks
- fixed some false positves for unknown core files (backup files, etc)
- added new icon for “unknown” file type different from “malware” type
- fixed warning on PHP versions > 8.1
- improved directory traversal for some directory symlinks
- fixed bug on standalone installs not resolving css files correctly
- reduced complexity of malware scan dashboard page
3.9.10
- fixed issue mixed type issue for older PHP versions (<= 7.4)
- begin internationalization work
- remove dependency on debug
3.9.9
- Improved malware detection and removed most false positives
- Improved performance of quick scan mode
- Reduced filesystem impact of both standard and quick scans
- Improved Bot auto learning and dynamic domain resolution
3.9.6
- DIVI builder theme support (support self included iframes)
- deactivation effect
- bug fix for some older versions of curl
3.9.5
- Improved logging for download errors
- Fixed missing blog-header.php hash codes
- Added Support for command line malware scan
- Improved support for WPEngine
- Improved order of operations to increase performance
- Support for XML and text data in Post Data
- Bypass some DNS lookups to dashboard page
- Improved include file malware scanning
- Fix stand-alone password install problem
- Added command line malware scanner
3.9.4
- fixed compatibility problem with WPEngine
- improved bot blocking compatibility
3.9.3
- improved bot detection and handling
- remove old bot exceptions from exception list
- fixed a bug on tagging and allowing unknown bots on the bot control screen
- removed inline svg images from malware frequency scanning
3.9.2
- revamped malware scanning. reduces false positives for PRO and 3rd party plugins
- new advanced malware scanning mode with configurable scan settings
- async http requests on malware scanning
3.7.1
- reduce malware false positives
- added detection for image include malware
- improved machine learning dataset
- added __wakeup() handlers for all classes with magic methods to prevent inclusion in POP chain
- improved bot listing formatting to support longer data formats
- better handling of some server temporary failures (filesystem, network, etc)
3.6.4
- improved malware detection
- improved support for some smaller hosting providers
- improved bot authentication during learning
3.6.3
- various PHP warning fixes
3.6.2
- Improve support for WordPress installs in path sub directory
- Performance improvement for user capability check
- Small warning fixes for PHP 8.1
3.6.1
- New bot control management page
- Improved settings and RASP configuration
- Improved upgrade process to keep all config data between upgrades, re-installs
- New hidden (secret) file support for nginx without modifying file permissions
(configuration data is now stored in a random hashed directory) - Small bug fixes on malware scanning for files in root directory
- Improved support for PHP 7.2
3.5.3
- Added over 600 known bots with network identification
- Improved malware scanning support for unknown files
- Added additional scan locations
- Added JavaScript malware scanning
3.0.8
- Database Malware Scanner Support
- Offsite database backups
- Fixes for some apache server installs
- Support for malware scanning plugins off the WordPress repository
- Added support and small fixes for PHP 8.1
- Improved malicious file upload scanning
- Improved basic settings and advanced settings page
3.0.6
- Added a pretty error page for browsers that do not support JavaScript when JavaScript verification is enabled.
3.0.4
- Minor bug fixes for corner cases
3.0.1
- Added database malware scanning support for over 2.5 million domains
2.3.5
- improved configuration wizard and css styles
2.3.4
- Malware Scanner Support
- Fixed a bug in browser verification on mobile safari.
2.3.3
- Added CSS styles to the blocking page
2.1.2
- Added plugin vulnerability notifications. These will check over 3500 active CVE advisories
for any known security issues in your plugins or themes - Improved upgrade process which could forget some settings on upgrade
- Fixed a possible rare false positive on base64 encoded data
- Improved learning mode to find more false positives
- Fixed a warning on PHP 8.x with undefined variable for alerts from IPs with no associated country
(localhost) - Fixed a bug which incorrectly reported the currently viewed alert page number range on the dashboard screen
2.1.0
- Several bug fixes
- Improvements to malware scanning, added additional files to scan list
- Fixed bug adding additional allowed domains on settings page
2.0.1
- Implemented setup wizards and online help functions.
- Added auto-learning exceptions for new installs to prevent possibility of false-positives..
- Workflow and usability improvements
1.9.7
- fixed an issue that could cause false positive when non administrators
were editing posts. This check has been expanded to authors as well. - fixed an issue that was causing extra padding in config.ini files
- added support for auto-discovering bots to whitelist
- reduced the maximum size of saved blocked data
1.9.6
- fix for WordPress source code path resolution
- use CMS default script inclusion system for admin pages
1.9.5
- added initial support templates for custom CMS
- refactored escaping on MFA page
1.9.4
- fixed an issue which could allow admin requests to be rate limited
- refactored malware scanner to support custom CMS
1.9.3
- added support for redirect url on MFA login page
- fixed issue with MFA login submission
- added support for Content Security Policy WordPress integration
- WordPress MFA login support complete
- PHP file write blocks are now logged in the dashboard
1.9.2
- improved support for alternate content management systems
- removed direct $_SERVER, $_GET, $_POST access and replace with filter_input
- fixed issue that could cause malware download to fail with expired access token
1.9.1
- improved install logging
- additional tests for installation procedure
1.9.0
- added SQL auditing feature. Currently this is an advanced toggle only available
by editing the config.ini. Planned features: SQL Injection Detection, CC data
access, replay log for DB restores - namespaced all defines to prevent any possible name collisions
- added WordPress plugin and theme enumeration blocking
- refactored several echo lines to remove dead code and xss encode on the same line
- added fix for a bug in php >=8.0 <= 8.1 where splat operator on variables containing :
would be incorrectly interpreted by PHP 8.0 as a named operator. - added support for cloudflare real connecting IP
- plugins not registered at wordpress.org are now rolled into a single malware line
1.8.9
- upgraded bootstrap and chart.js to latest stable releases
- refactored all API methods to be pure and testable
- refactored malware detection to allow detecting malware on non-WordPress installs
- updated all WordPress path resolutions
- added code to ensure config.ini is not web readable even when .htaccess is disabled
- INI settings: reset realpath.cache_size to system size when used with openbase_dir
- special handling of DOCUMENT_ROOT for WordPress
- improvements to installing always on protection on Nginx systems
- make config.ini unreadable even on systems that do not support .htaccess
1.8.6
- added additional WordPress abstractions as requested by WordPress team
- upgraded bootstrap css files
- abstracted wordpress plugin with pure implementations and additional unit tests
1.8.5
- refactored several functions with pure implementations and added unit tests
- refactored views to use new template system
- refactored wordpress integration to use standard plugin architecture
- moved all dashboard javascript, image, css files into the distribution
- removed dead code
- removed a warning for php 8.1
1.8.3
- Added support to enable always-on from settings page
- Added support for WordPress Engine
- Fixed bug where rotating encryption keys would prevent new signatures from downloading for up to a day
1.8.0
- Improved support for PHP 8.0
- improved settings page
- improved malware scanner
- additional whitelist SEO bots
- improved auto-detection of server support
1.7.3
- First public release of BitFire WordPress security plugin